
Take care of IT security now:
Cyber security for logistics companies


Cyber attacks have caused €179 billion in damages to German companies in 2023, according to an alarming study by the industry association Bitkom. Two-thirds of companies even see cyber crime as a threat to their existence. Logistics, as one of the world's largest and highest-turnover industries, is increasingly falling victim to such attacks.
As attackers are using ever more complex tactics and technologies to circumvent conventional security controls, IT security requirements are constantly changing. You should be prepared for this and pursue a holistic cyber security strategy. This is the only way to quickly detect such attacks on your company and to limit the damage.
Always be one step ahead of attackers and utilise logineer’s expertise in all matters of IT security. We offer you the many years of experience of our parent company q.beyond AG with cyber security services and combine it with our special industry knowledge. This ensures you get IT security from a single source which is tailored to your needs as a logistics company. Upon request we can support you through the entire process. We advise you on the planning as well as on the set up and support you in the operation of your state-of-the-art cyber security solutions.
Increasingly complex cyber attacks: Challenges for logistics companies
Regardless of the size of the company, logistics businesses are increasingly becoming the target of cyber criminals:
- The logistics industry is the link in the supply chain that is particularly vulnerable - because many partner organisations that are networked globally work together and exchange sensitive data over a wide variety of technical systems.
- Outdated operating and office programmes, as well as servers, are particularly large areas of attack.
- Increasing digitalisation, automation and IT networking, without which logistics processes are no longer conceivable, are leading to new security risks.
- Attackers often gain access to IT systems not by exploiting security gaps in the infrastructure, but by tricking employees.
Cyber attacks range from data espionage, to cyber vandalism right through to cyber war. The attackers sabotage processes, steal intellectual property, destroy data or interfaces and demand ransom money for their restoration - Keyword: Ransomware. It’s especially dangerous if the cyber attack remains undetected, enabling data to be stolen or destroyed unhindered.
The consequences are often devastating: attacks on IT company networks lead to production and supply failures, and in the worst case to a complete shutdown of operations. Often important information is lost forever, resulting in high financial losses and considerable damage to the company’s image. As such, cyber attacks can threaten the existence of many companies.
Strengthen your supply chain’s resilience with cyber security!
This is particularly important in view of the threat situation: ask yourself not whether your company will be affected by a cyber attack, but rather when this might happen.
As cyber criminals attack not only at the technological level, but also at the organisational and human levels - by targeting processes and employees - there will never be 100% security.
It is therefore all the more important that you view defence as a company-wide task and test, optimise and secure all your company’s technologies, processes, interfaces and communication channels.
It is no longer enough to just install basic technical protection such as simple firewalls, for example. Instead, you should be using comprehensive and state-of-the-art cyber security solutions and planning for this from the very start during the digital transformation.
When you increase the resilience of your IT infrastructure, you are also protecting the supply chains against cyber attacks and therefore ensuring greater security in logistics.
logineer: Holistic cyber security strategy for logistics companies
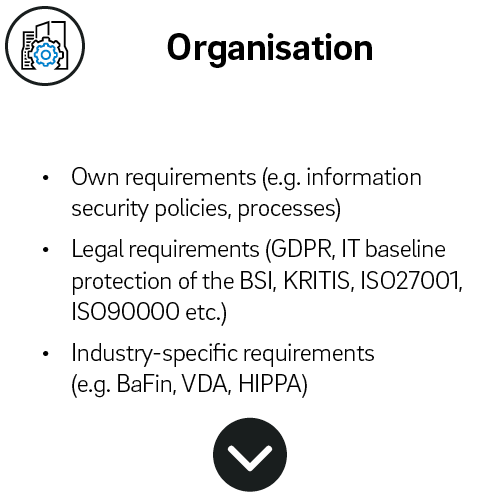
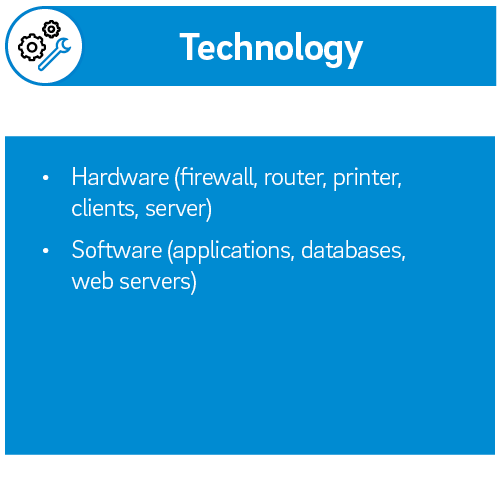
We work together with you to create a comprehensive cyber security strategy that considers your company as an organisation and your employees, as well as your IT landscape.
For each of these three areas - organisation, people, technology - we recommend a three-stage process that involves planning, development and implementing respectively.
In the planning and development phases, we provide you with comprehensive advice; in the implementation phase we support you with the IT operation of your cyber security solutions. When doing so, we always take into account your specific requirements as a logistics company and the security needs of the supply chain.
- Planning = Management consulting: among other things, identification of external requirements e.g. GDPR or ISMS and other GRC topics (GRC = Governance, Risk & Compliance) as well as strategy for the introduction of training and the procurement of software and hardware
- Development = Cyber security consulting: including identification of knowledge gaps in the workforce and gap analysis, as well as analysis of the market for security services
- Implementation = Cyber Security operations: including documentation, training, technical assistance as well as the implementation of cutting-edge cyber security solutions e.g. Vulnerability Management, SIEM (Security Information and Event Management) and EDR (Extended Detection and Response)
Cyber security requires a holistic view



Security Awareness Training: Increasing the safety awareness of your employees
A company achieves security awareness primarily through prevention - in other words, by educating the workforce. Only when staff are fully informed about possible misconduct as well as cyber threats and on how to act correctly can an organisation reach a high level of security awareness.
The employees gain an increased awareness on the topics of cyber security and data protection in focused training courses, they are thus empowered to prevent security incidents. Through their actions, they make an important contribution to the protection of the company.
Downloadlogineer cyber security services for optimal security of your IT infrastructure
Vulnerability Management Service:
Our Vulnerability Management Service is the basic building block of a comprehensive cyber security strategy. Using state-of-the-art IT tools, we find and eliminate vulnerabilities throughout your entire IT – in the hardware and software, as well as in networks and Shadow IT. When doing so, we take into account the special features of international logistics and also bring our special industry knowledge in the area of IT security.
Extended Detection and Response (EDR):
EDR is a further development of the virus scanner. With it, we can protect all end-user devices connected to your corporate network against cyber threats. As the solution detects threats in real time, it is possible to take defensive actions and detect harm at the outset. This way negative effects can be quickly minimized.
logineer – Your IT partner for cyber security services in logistics companies
- Long-standing experience: We offer our customers comprehensive expertise in identifying and eliminating IT vulnerabilities. This enables them to effectively secure their digital infrastructure against attacks and make it more resilient.
- Holistic cyber security from a single source: logineer’s offering ranges from strategic consultancy to the practical implementation of jointly defined solutions, including training for employees.
- Outstanding solutions: Our cyber security services have been tested many times and are regularly certified by renowned institutes (including ISO27001, ISO27014, ISO9001).
- Round the clock protection: Our cyber security services work continuously and operate reliably both preventively and in the event of an attack. In the event of a cyber attack, we are available around the clock to prevent or limit damage.
Do you have any questions or would you like a consultation?
Logineer smartens up logistics specialists operating on the international stage. Our biggest plus for you: Our combination of IT know-how and long-term experience in logistics. Our 200 IT and logistics experts build your digital infrastructure, making sure that your data and information flow smoothly across borders and time zones.
Just give us a call! With logineer as a subsidiary of q.beyond, an IT service provider holding many years of experience in cyber security services, you have a partner by your side who can help you protect yourself as best as possible.